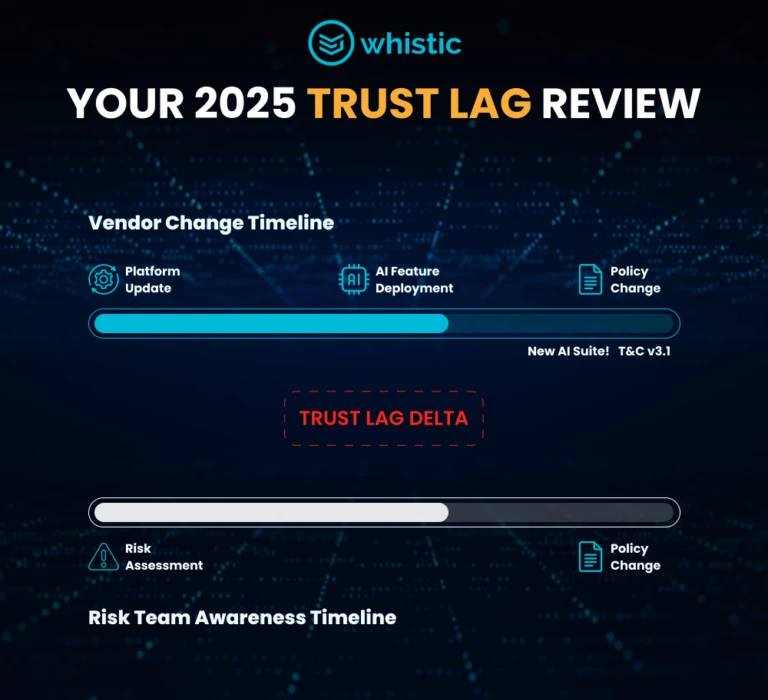
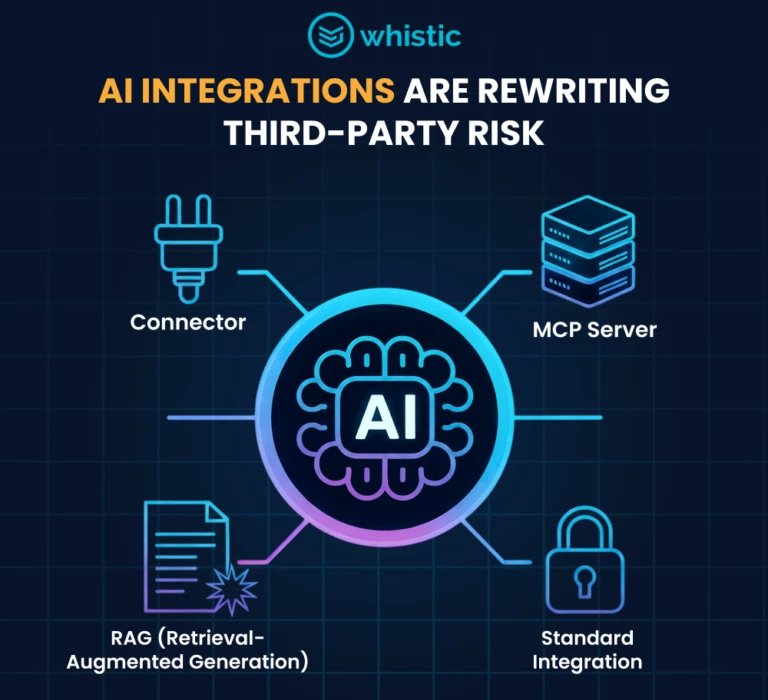
How Whistic Helps Organizations Manage Third-Party Risk Across Expanding Vendor Ecosystems
Whistic centralizes security evidence and prioritizes exposure-based assessments to streamline vendor onboarding while reducing third-party risk blind spots.
Read More