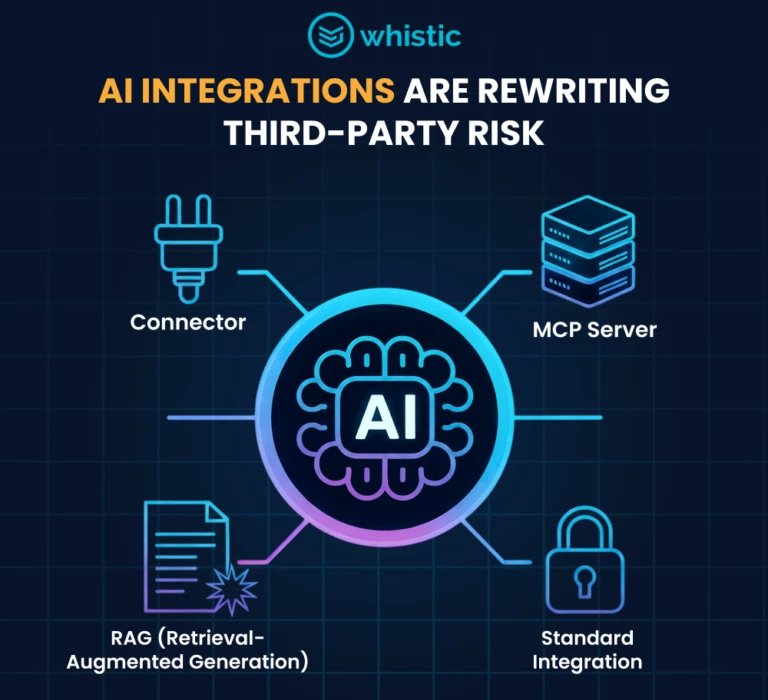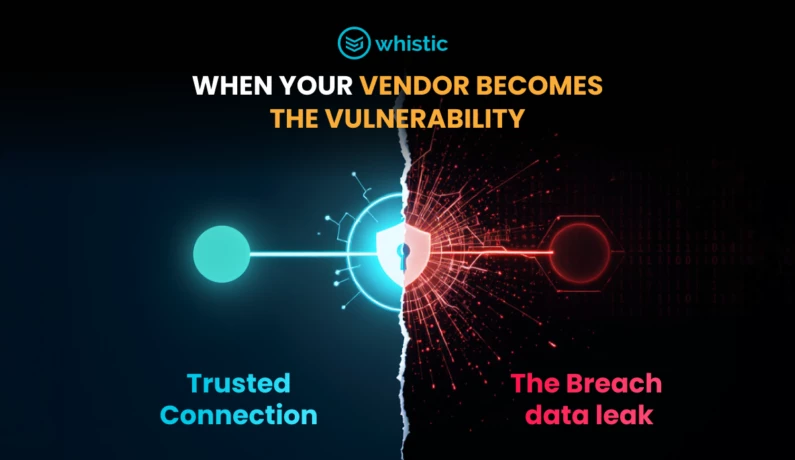
When Your Vendor Becomes the Vulnerability: Lessons from the Discord Breach
When trusted vendors become vulnerabilities, risk multiplies fast. Learn how Whistic’s automated assessments and Trust Catalog help teams prevent breaches and build real-time trust.
Read More